Test and secure your security controls so you can be ready for a real-world attack.
Cyber attacks can devastate your organization if you’re not
prepared. Do you know how your company would respond
to a real-world ransomware, supply chain, or other attacks?
Only 20% of adversary cyber-attack techniques are actually identified by detection and alerting tools due to misconfigurations, changes in tool controls, alerting failures,
and other dynamic factors.
Leveraging the power of EITS Attack Simulation as a Service, EITS can simulate a variety of attack chains from initial access to data exfiltration, visualizing security control failures, and comprehensive directions for remediation to remove coverage blind spots.
- Providing visibility into security tools posture and effectiveness.
- Simulating real-world attacks to verify they will work as expected.
- Delivering detection and prevention improvement guidance.
- Validating security tool changes with evidence to show improvement.
REMOVE SECURITY BLINDSPOTS BEFORE THE ATTACK.
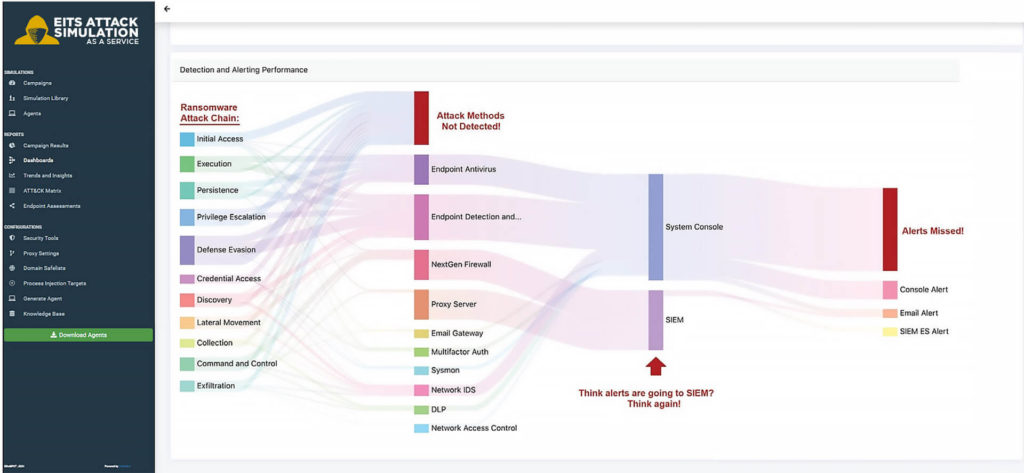
EITS Attack Simulation as a Service clearly visualizes gaps in your security configuration.
TRANSFORM YOUR NETWORK DEFENDERS WITH CONTINUOUS TESTING.
SERVICE OVERVIEW
Our attack simulation service executes real-world cyber-attack techniques to test whether detection and alerting controls will respond as expected, with hands-on training for the network defense team with various
attack techniques and options to detect attack activity.
SIMULATION TECHNOLOGY TOUCHPOINTS
Customer Endpoints & EITS Agents
EITS simulates attacks via agents”, which are run on a a small sample of endpoint(s) that the customer selects.
EITS simulates attacks via agents”, which are run on a a small sample of endpoint(s) that the customer selects.
Simulation & Defend Platform
Simulation detection and alerting results are scored in
the EITS web application, which visualizes security stack
coverage and provides remediation recommendations for
improvement.
Empower Network Defenders with
EITS Attack Simulation
As a Service.
- Efficient 8 hour exercise
- Simulates threat hunting & remediation on your production network
- Delivers detailed, comprehensive reporting:
- Executive Overview
- Detailed pass/fail ratings
- Identification of gaps
- Recommendations for improvement