Asset and Application Inventory
SANS critical security controls 1 and 2 define that an organization needs to have positive control of their assets
and applications in order to effectively develop a comprehensive security program.
You can't secure what you don't see.
Reclaim your organizational control.
Comprehensive visibility into network-attached devices is critical to understanding vulnerabilities and risks associated with those endpoints. With EITS’ Asset and Application Inventory in place, you can mitigate the risk of newly identified devices, addressing vulnerabilities and potential pitfalls.
Let us help you address the Inventory of all applications running on your network. Application inventory is key to the identification of sensitive data, and how it is being consumed, stored, and protected.
Inventory across cloud environments is key to identification of all assets and applications. Our integration capabilities across Software as a Service (SaaS), Infrastructure as a Service (IaaS) and Platform as a Service (PaaS) enable us to achieve true 100% inventory of all workloads your organization is supporting.
When you choose EITS, we provide:
- Traffic & logs digested from multiple sources, which provide a more comprehensive analysis.
- In-depth and detailed data collected on all network devices and connected devices.
- Not limited to specific technology platforms, the discovery will find & analyze all devices with an IP address.
- Certified expert and in-depth analysis of what's collected.
- Ability to identify well-known vulnerabilities and detect common and weak clear text passwords in use across the network.
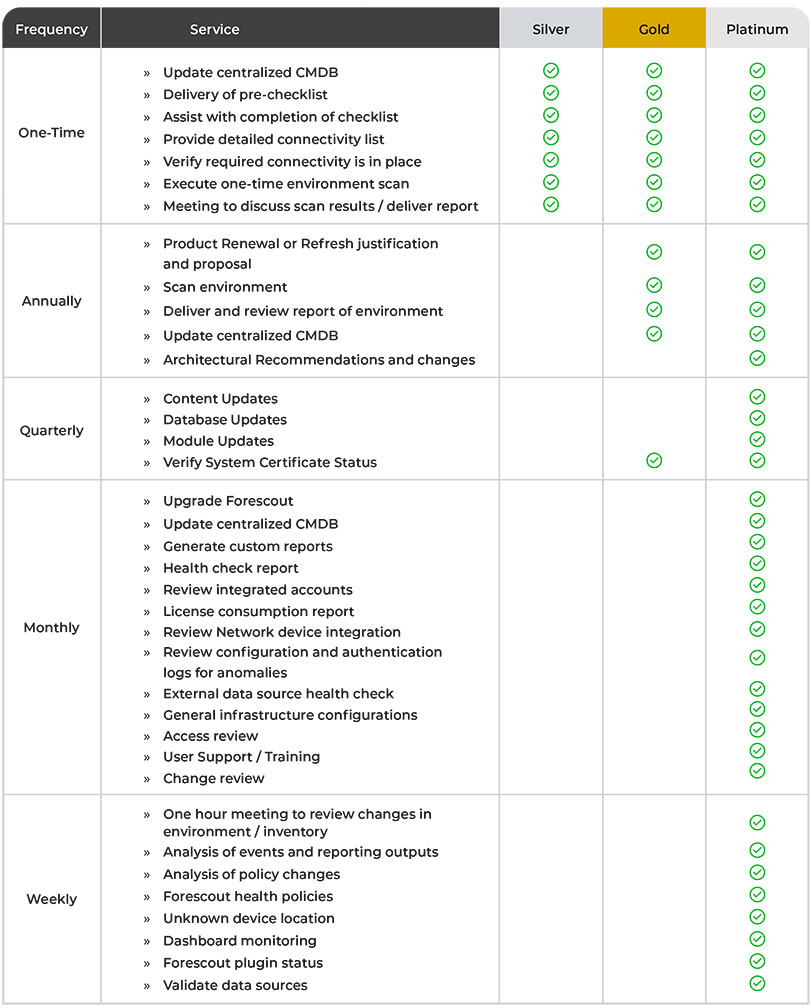
Managed Services Plans